Which of the Following Are True Statements About Phishing Attacks
Remote attacks requiring user action. It is usually performed through email.
The case is based on DDoS denial of services attacks on the enterprise website created by botnets.

. To limit the damage you should immediately change any compromised passwords and disconnect from the network any computer or device that could be infected with malware because of the phishing attack. 13 you have copied a software package computer program from a friend without paying for it you are guilty of software piracy. An input device sends information to the computer and an output device sends information to the computer.
Theyre important to keep. B Multifactor authentication systems are. Remote attacks requiring no user action.
Q2 2018 41 of successful o nline e-commerce and mobile fraud attacks are enabled by phishing scams. Question 11 1 point Which of the following statements is true. Upon connecting your Government-issued laptop to a public wireless connection what should you immediately do.
I- The network is fault tolerant. Which of the following statements is true of phishing emails. Which of the following statements is true.
The security office decides to provide training to all users in phishing prevention. Asked Apr 30. Which of the following statements are true about this network.
The goal is to steal sensitive data like credit card and login information or to install malware on the victims machine. According to the case Something Phish-y which of the following is a true statement about the case. The information is then used to access important accounts and can result in identity theft and.
3 Phishing is an example of repudiation attacks. Connect to the Government Virtual Private Network VPN. Whereas phishing attacks are ____ denial of service attacks are ____.
Which if the following is not a common risk mitigation strategy. Because of the massive audience the email content must be generic enough to dupe a good number of them. According to RSAs Quarterly Fraud Report.
Phishing attacks can take many different forms including. II- Computers B and F need to first communicate with at least one other devices in order to communicate with each other. Choose all that apply.
A coworker has asked if you want to download a programmers game to play at work. What is TRUE of a phishing attack. Which of the following are true statements about phishing attacks.
4 E-mail spam is an example of man-in-the-middle attacks. Which of the following may be part of a phishing attack. Which of the following statements is true of phishing emails.
Phishing is among the biggest cyber threats facing organisations. Phishing attacks are the practice of sending fraudulent communications that appear to come from a reputable source. True statements on phishing attempts identification Ensuring e-mail is from a trusted legitimate e-mail address source.
Phishing attacks are very simila. Which of the following statements is true. Remote attacks requiring user action remote attacks requiring no user action.
A _____ is a remote attack requiring user action. Theyre important to keep. Phishing is a type of social engineering attack where the attacker uses impersonation to trick the target into giving up information transferring money or downloading malware.
Select all that are true. You can avoid being phished following phishing prevention best practices. A phishing attack is an attempt to access an account by repeatedly trying different passwords.
Which statement is true of phishing. Select the best answer A. Which of the following are true statements regarding identification of phishing attempts.
Here are several statements about MIME. On the other hand spear phishing is customized to the victims so scammers must do extensive research to be convincing. A targeted phishing attack against a known individual.
Which of the following is a type of phishing attack that specifically targets highranking corporate executives. For instance if a person frequents a golf course the spoofed email. Phishing is a cybercrime in which a target or targets are contacted by email telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information banking and credit card details and passwords.
II - Phishing attacks can be defended against using data compression. An input device sends information to the computer and an output device receives information from the computer. Group of answer choices.
Theyre the same thing as junk mail. Phishing emails frequently take advantage of high-profile catastrophes reported in the newsWhich of the following principles BEST describes the weakness being exploited. According to Proofpoints 2021 State of the Phish Report more than 80 of organisations fell victim to a phishing attack last year.
1 Denial of service attacks may harm the goal of confidentiality. A Multifactor authentication systems are more reliable and less expensive than single-factor. Examples include using actual profile pictures in phishing emails creating fake social media profiles and doxing potential victims social media accounts.
Verifying spelling and grammar. Phishing can be an email with a hyperlink as bait. The case uses a fictional company that revolves around the Internet Crime Complain Center b.
Also check bank or credit card statements regularly to make sure fraudulent transactions do not show up there. They pretend to need information and use it for harm. Even if you have not been phished this is a wise course of action to follow.
They come from trusted sources. Whaling is a type of spear phishing attack used to retrieve sensitive information from highranking executives of a corporation. Phishing e-mail attacks have caused severe harm to a company.
They come from trusted sources. Criminals use phishing attacks to try to get at your personal information. Theyre the same thing as junk mail.
Select all that apply. 12 phishing attacks are ____ denial of service attacks are ____. I - Phishing attacks are characterized by communication from one person trying to trick another person into divulging personal information.
They pretend to need information and use it for harm. One of the most frustrating things about this is that most people know what phishing is and how it works but many still get caught out. C A log in request that collects secret authentication credentials.
Deleting the email will not stop any damage the attack may have caused. 2 Unauthorized alteration may harm the goal of message integrity. Risk management identifies controls and minimizes the impact of threats to the organizations information security.
If a single connection fails any two devices can still communicate.

Cyber Safety Cyber Safety Security Tips Address Icon

Cyber Security This Poster Teaches People How To Identify Phishing And Spear Phishing Emails It Provides An Example Teaching Posters Security Cyber Security

Wordpress Bug Could Expose Users Of 20 000 Websites To Phishing Attacks Attacks Bug Expose Phishing Users Webs In 2022 Mail Template Array Methods Cyber Security

What Is A Phishing Attack Cyber Security Cyber Security Program Online Assessments

Cuanta Gente Cae En La Trampa Del Phishing Infografia Infographic Internet Tics Y Formacion Cyber Security Awareness Email Security Cyber Security

Phishing Scams Prevention Tips And Examples

How To Spot A Phish Infographic Phishme Cyber Security Education Cyber Security Awareness Infographic

Information Security Phishing Examples Information Technology Services Binghamton University
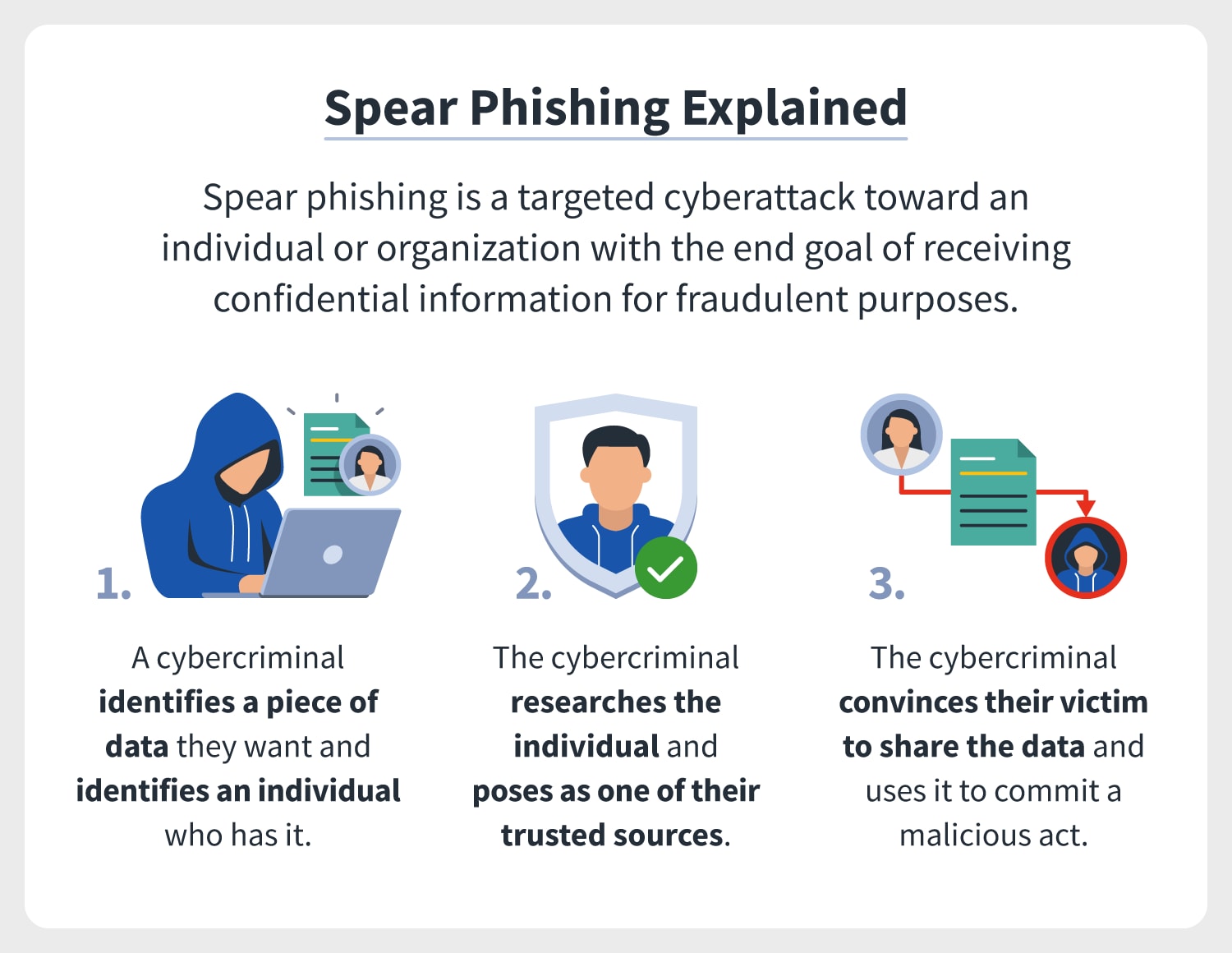
Spear Phishing A Definition Plus Differences Between Phishing And Spear Phishing Norton

Repost Thecybersecurityhub 10 Ways To Detect Phishing Emails Cybersecurity Infosec C Cyber Security Awareness Cyber Awareness Cyber Security

How To Recognize Phishing Mails Shieldit

True Cyber Resilience Cyber Threat Cyber Attack Cyber
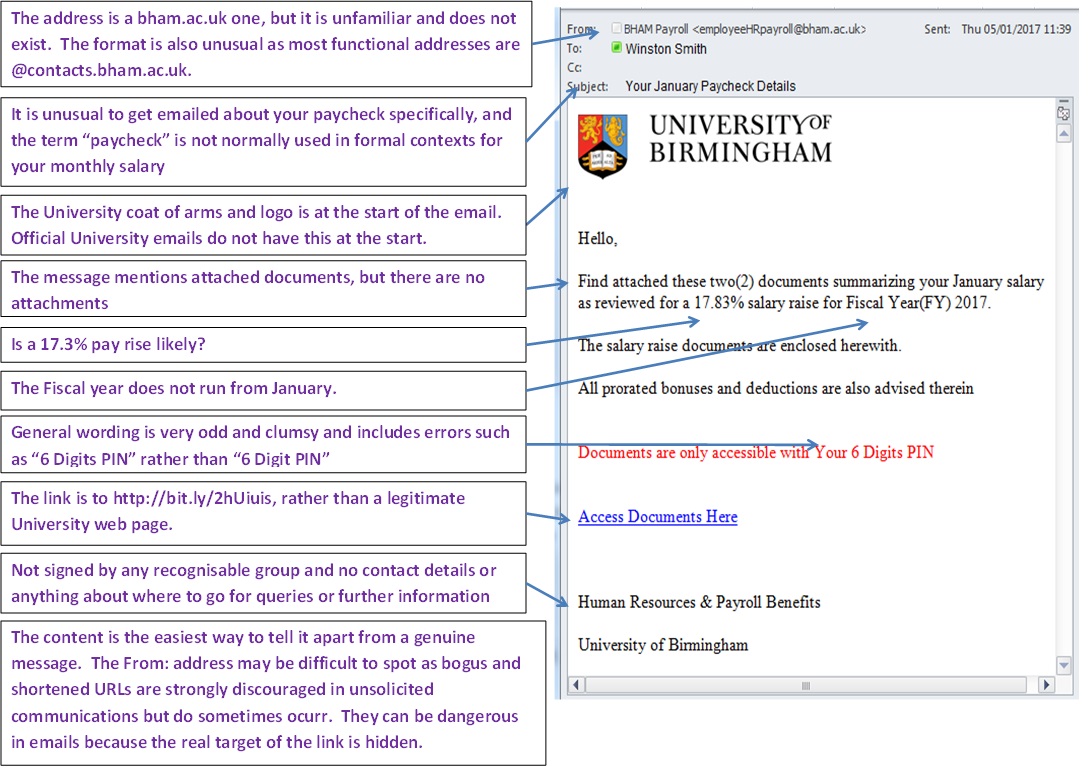
Pay Rise Too Good To Be True It Security

Phishing Fraud Cyber Security Awareness Computer Security Cyber Security Education

How To Avoid Cell Phone Phishing Attacks Cyber Security Technology Cyber Security Computer Generation




:max_bytes(150000):strip_icc()/Netflishphishingscamemail-2f634e8596b14a64882a46d14577ed13.jpg)
Comments
Post a Comment